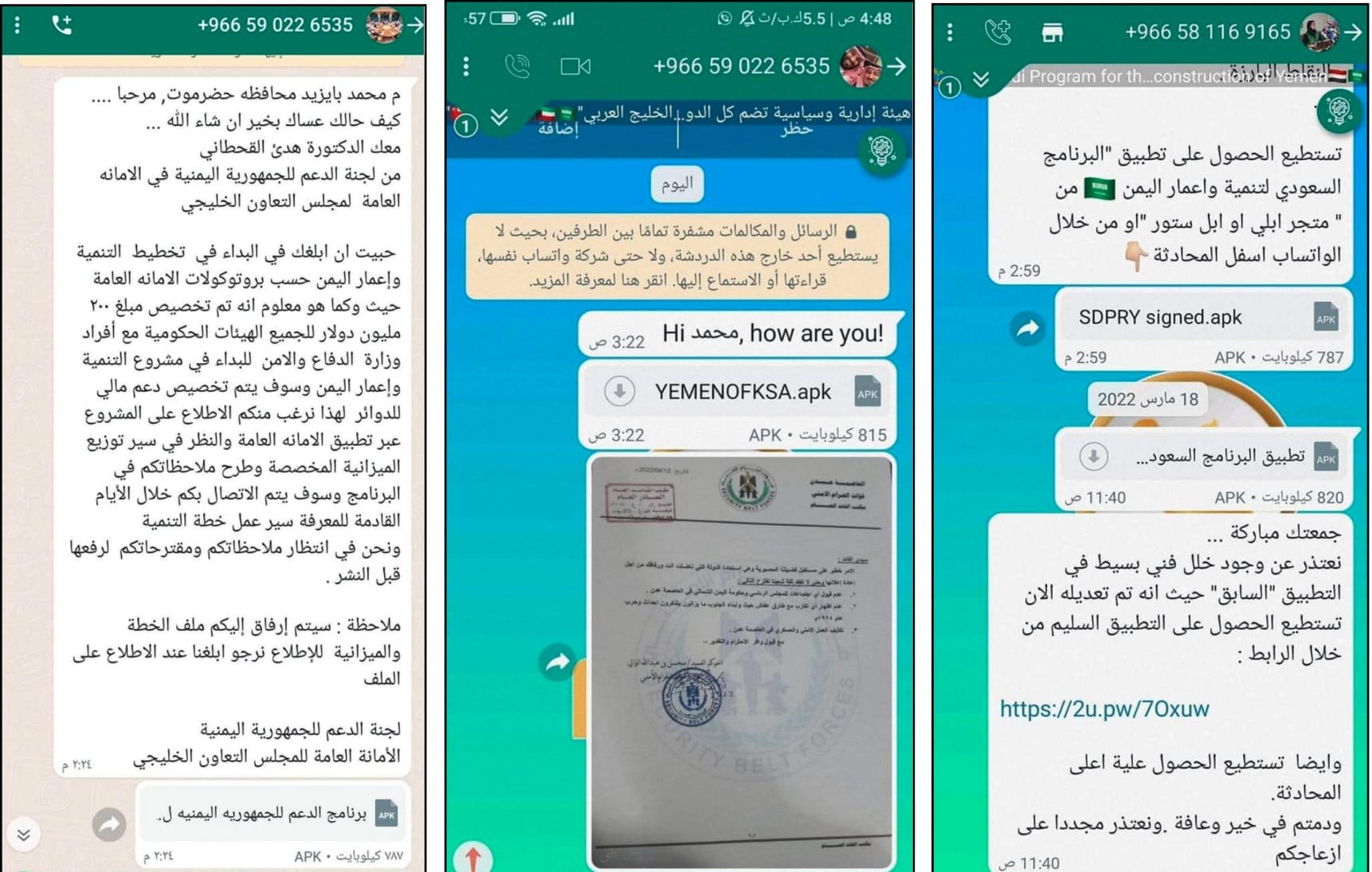
Snapshots for spy conversations sent by the hacking group to some of its victims (Aden Hurah)
19-05-2023 at 6 PM Aden Time

South24 (Aden)
A likely Pro-Houthi hacking group, known as "Oil Alpha" targeted Yemeni individuals, media platforms, and non-profit humanitarian organizations in the Arabian Peninsula via "WhatsApp" as part of a digital espionage campaign, “Record Future”, a company specializing in cybersecurity, disclosed.
According to an extended report published by the company Tuesday, Oil Alpha's operations "reportedly included targeting persons attending Saudi Arabian government-led negotiations; coupled with the use of spoofed Android applications mimicking entities tied to the Saudi Arabian government, and a UAE humanitarian organization".
Moreover, the hacking group forged documents that spoofed the name of the Security Belt Forces affiliated with the STC in Aden. "South24 Center '' noticed that these documents included decisions attributed to Mohsen Al-Wali, the Commander of the aforementioned forces. They aimed at inciting against the new-formed PLC. These messages were attached along with a spy Android application that spoofed the name of an organization.
"Record Future" believes that the hacking group, Oil Alpha", supports the Houthi agenda. It said that the group "relied on infrastructure associated with the Public Telecommunication Corporation (PTC), a Yemeni government-owned enterprise reported to be under the direct control of the Houthi authorities". It added that all dynamic "DNS" domains were assigned to "IP" addresses belonging to the Yemeni Public Telecommunication Corporation.
The domains used by the hacking group to target its victims refer to the Yemeni Public Telecommunication Corporation occupied by the Houthis (A snapshot from Record Future Report, South24 Center)
The company, specializing in monitoring cyber threats, republished pictures for some of these chats that were previously posted in April 2022 by the well-known Southern Facebook platform "Aden Hura".
Record Future added that “OilAlpha” used encrypted chat messengers like WhatsApp to launch social engineering attacks against its targets. It has also used URL link shorteners. Per victimology assessment, a majority of the targeted entities were Arabic-language speakers and operated Android devices".
According to the company, "the hacking group targeted the devices of some political representatives and journalists at the Riyadh Consultations with remote access tools (RATs) to install spyware such as SpyNote and SpyMax".
For its part, "CyberScoop", the website specializing in cybersecurity said: "There is no indication of how successful OilAlpha’s operations have been since it started tracking the outfit. The firm believes the group has also spoofed Saudi Arabian organizations such as the King Khalid Foundation, King Salman Humanitarian Aid and Relief Centre, and Project MASAM which removes landmines in the region". "South24 Center" noted that the group spoofed the names of official bodies affiliated with the Gulf Cooperation Council.
South24 Center also noted that the targets included Hadrami figures. One conversation included information about "200 million dollars" for the reconstruction of Yemen as it claimed. The message was identified under the name of Huda Al-Qahtani as a representative of what was described as "the Support Committee for the Republic of Yemen in the General Secretariat of the Gulf Cooperation Council".
"Record Future" also said that the hacking group spoofed requests attributed to non-governmental organizations such as UN Children's Emergency Fund, the Norwegian Refugee Council, and the Red Crescent. These organizations manage or coordinate responses to crises and humanitarian work in Yemen.
"Record Future" indicated that there has been enough evidence to determine if Yemeni hackers carried out the attack or other threat groups in the region.
It pointed out that external threat groups such as Hezbollah (The Lebanese or the Iraqi” or even the Iranian operators that support the "Islamic Revolutionary Guards" likely led this threat activity. This is based on the fact that these groups have entrenched interests in the outcome of the Yemeni war.